CLIENT SUCCESS STORIES
The Customer - SAFARICOM LTD
 Safaricom is Kenya’s first and leading Cellular Operator and has a significant shareholding by Vodaphone the world’s leargest cellular operator. Safaricom boasts of a subscriber base of close to over 4.5 million and have encountered phenomenal growth over the past two years. Safaricom is Kenya’s first and leading Cellular Operator and has a significant shareholding by Vodaphone the world’s leargest cellular operator. Safaricom boasts of a subscriber base of close to over 4.5 million and have encountered phenomenal growth over the past two years.
The Challenge
As the world becomes increasingly connected, risk rises accordingly. In response, businesses need a means to manage risk without disrupting normal operations or having to invest more money in a security solution than is necessary. By bringing a wide range of security technologies – active blocking, malicious code control (active content and/or antivirus), PKI, VPN, vulnerability assessment, policy distribution and enforcement, IDS, application protection, and security decision support – into a common framework, then packaging that framework to address specific business needs and operational IT functions, ComputerPoint has built significant internal competencies to address security challenges of our customers to align our solution as a measurable business benefit to customers. From the 2001 CSI/FBI Computer Crime and Security Survey, the following facts emerged:-
- 91 percentage of respondents detected computer security breaches within the last 12 months
- 64 percent of respondents acknowledged financial losses due to computer breaches. The most serious financial losses occurred through theft of proprietary information and financial fraud.
- 70 percent of respondents said their internet connection was a frequent point of attack, up from 59 percent in 2000.
Taking charge of addressing their Enterprise Security needs, Safaricom desired the deployment of their primary security building block in a reliable FireWall solution.
The Solution
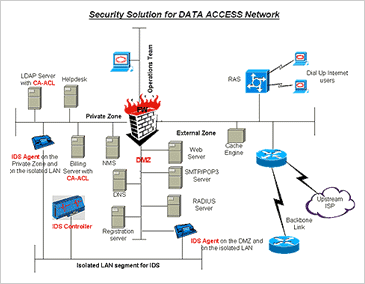
After a diligent evaluation of security solutions from multiple vendors, Safaricom contracted ComputerPoint to deploy the Cisco PIX firewall. The network infrastructure included four primary servers which had access to the Internet. These include the MS Exchange Mail Server, MS Proxy Server, MS Norton Antivirus Server and the Server used for File transfer (FTP) between Safaricom and Multinational Automated Clearing House (MACH)
While the Proxy Server and the Norton Antivirus server always initiate connections to the Internet but don’t receive connections initiated from the Internet, the Mail and FTP Server also receive connections initiated from the Internet.
Other computers at Safaricom access the Internet through the Proxy server.
The Firewall configuration was therefore designed to allow all traffic from the above Servers going to the Internet, while only allowing connections from the Internet that are destined for the Mail server and the FTP server.
The following considerations were implemented on the PIX Firewall:
- The inside and outside interfaces were configured to use 100BaseTX media for communication with the Internal network Ethernet Switch, as well as the Router connecting Safaricom to UUNET.
- The PIX was configured to use Port Address Translation (PAT), a type of NAT where several inside addresses share one global address. The Global address configured was the address of the outside interface of the PIX.
- The inside addresses that were allowed to communicate on the Internet through NAT were the whole subnet.
- The TCP Intercept feature was configured for the Mail and FTP servers, with a limit of 100 uncompleted connections.
- An access list was created for traffic initiated from the Internet, allowing the UUNET SMTP server to access the Safaricom Mail Server, and the MACH FTP server to access the Safaricom FTP Server. This access list was used on the outside interface.
- A default route was configured, to send all traffic from the inside mail network to the router connecting UUNET.
- A telnet and enable password were set by Safaricom Personnel.
Post deployment the entire solution was tested as follows:
- The Proxy Server was tested and confirmed that it could access the Internet through the Firewall.
- The Mail server was tested and confirmed that it could send mail through the Firewall. It was also tested and confirmed that it could receive mail through the Firewall.
- The Norton Antivirus server was tested and confirmed that it could access the Internet for updates.
- The Safaricom FTP server was tested and confirmed that it could access the MACH FTP server. Subsequently, it was confirmed that the MACH FTP server could also access the Safaricom FTP server
|